Most companies spend significant resources on internal cybersecurity (rightfully so), for example, vulnerability scans, SIEM, centralized log management, or end-user security awareness trainings, and lot more. But unfortunately, they also tend to make a cardinal mistake of not extending the same diligence towards their vendors or third parties.
Sadly, they too often don’t seem to realize the full magnitude of dangers this approach involves. After internal employees, your vendors are the second weakest link of your (security) chain.
If your company chooses not to verify the security of its vendors/third parties, then it is significantly increasing its own RISK while reducing the security assurance of its own information systems.
It is essential for all security managers to realize that if a data-breach happens at your company and the cause of this breach is found to be at any of your third parties, it is still your company’s name and brand that is at risk. You are not absolved of your own legal responsibilities and your company may be penalized for this error.
What Damage Can Your Vendors Do To You?
For the answer consider the following:
• How much access each vendor individually has to your IT systems?
• How many controls you have established to contain their access?
• How much data is exposed to them? What is the criticality of that data to your company?
So many companies tend to outsource functions such as Accounting, Legal, etc. to vendors or third parties. If any of them gets unfair or unrestricted access to your IT systems, then in this example, you would be releasing highly private and potentially valuable data into unknown IT systems of your vendors, with unknown controls and unknown users. Don’t you think it is too much risk by default?
How can you be confident that your vendors take cybersecurity threats as seriously as you do? Or that they are even aware of them? The answer is that you can’t unless you address the issue upfront with them as part of your overall organizational cybersecurity strategy.
• In a survey by PricewaterhouseCoopers 63 percent of all cyber-attacks could be traced either directly or indirectly to third parties.
• According to an Opus and Ponemon Institute study, 59% of companies have experienced a data breach due to one of their vendors or third parties.
• According to a eSentire survey, nearly half of all organizations that experienced a data breach was caused by a third-party vendor.
The enormous magnitude of the SolarWinds incident is a perfect example of such a third-party risk issue.
There are so many cyber-attacks happening due to the weak cybersecurity implementation at your vendor(s) side. And this unfortunate reality is the inspiration behind writing this article.
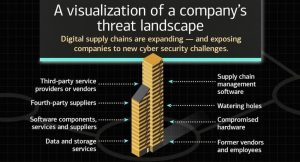
Some of your vendors may include cloud service providers, payment processing providers, or supply chain partners, and others; all of them must be considered for third-party security risk management.
What Should You Do?
Your company must develop a more robust stance on vendor management. If you are ready to build a truly effective and mature ‘Vendor Management Program’ then you must be willing to dedicate the time and resources also to do it right.
It will require you to develop the following:
1. A Vendor Management Policy
It should cover the objectives behind assessing the security at vendors, staff responsibilities, communication & reporting channels, and other core components of the overarching program.
2. Procedures (SOPs)
Along with the policy, your organization will need several defined procedures to implement and manage the vendor management program effectively.
These procedures can include:
• Assessment outlines/workflows
• Documentation management
• Evidence requirements, etc
3. A Ranking System
The idea of a ranking system is very simple. You would want to categorize your vendors based on their security readiness. Though there are many parameters to develop a reasonable ranking system, you are advised to look at the following factors seriously while devising this ranking system:
• Sensitivity of data they receive
• Volume of data they receive
• Importance of service they provide
4. Escalation Point
It is very important to assign some senior management personnel of your company who MUST be urgently notified using official channels, if any vendor is found lacking something serious in your security assessment of them. Experience has shown that most vendors will not take anybody else seriously other than a senior management person. And he or she should be capable and authorized to make any decision necessary to enforce expectations to/with the vendor. However, you still may need to assign some staff-members for routine vendors’ assessment and other liaisoning with regards to the relationship and information security.
5. Review of SLAs with Vendors
It is an understatement to say that your company must embed all important information security requirements into ‘Service Level Agreements (SLAs) to make all vendors obliged to meet your security needs from them.
IMPORTANT: All of the cybersecurity requirements of your company for vendors should be monitored by the specific teams or employees that work with these vendors regularly. The staff using the system or working with the vendor will be in the best position to notice abnormalities or contractual failings on the part of vendors.
6. Vendor Cyber Risk Assessments
A third-party cyber risk assessment works by providing an in-depth review of your vendors’ network security. The assessment is an evaluation and approval process that organizations use to determine if prospective vendors and suppliers can meet laid down standards and procedures once under contract.
The assessment helps your organization understand the level of risk associated with using a certain third or fourth-party vendor’s product or service.
Vendor management is a complex and time-intensive task which many organizations do not, and in many cases, cannot dedicate the time and resources to managing. For companies with a small number of vendors, this can be manageable, but most organizations will need additional support to create and implement these programs effectively. By dedicating resources to developing a program, your organization can begin to understand and eliminate the threats posed by your vendors/ third parties.
REMEMBER: It is extremely important to keep track of your ever-expanding vendor ecosystem, because digitization has fueled a massive increase in the number of suppliers for the average business.
Your vendors often have access to your company’s networks or supply it with software solutions or applications. A weakness in your vendor’s network or software – or even in the network of a fourth-party vendor – can open the door for cyber criminals. This means that a cyber event can originate several steps away from your company’s primary supply chain and still result in severe consequences to your company.
For FREE help designing a customized cybersecurity strategy for your organization, including vendor risk management, simply tell us what you’re trying to accomplish at Request A Consultation and we’ll make it happen. It really is that easy.





